Network plus practice test n10-008 – Prepare to conquer the Network+ Practice Test N10-008 with this comprehensive guide. Our engaging content will equip you with the knowledge and strategies to excel in the exam and advance your networking career.
From network fundamentals to cloud computing, this resource covers all the essential topics. Get ready to master networking concepts and achieve your certification goals.
Network+ Practice Test N10-008 Overview
The Network+ Practice Test N10-008 is a valuable resource for individuals preparing for the CompTIA Network+ certification exam. It provides a comprehensive assessment of the candidate’s knowledge and skills in networking fundamentals. By taking this practice test, candidates can identify areas where they need additional study and gain confidence in their readiness for the actual exam.The
Network+ Practice Test N10-008 consists of 90 multiple-choice questions, which must be completed within 90 minutes. The questions cover a wide range of topics related to networking, including:
Test Topics
- Network fundamentals
- Network technologies
- Network security
- Network troubleshooting and tools
The Network+ Practice Test N10-008 is an essential tool for candidates who want to succeed on the Network+ certification exam. By taking this practice test, candidates can improve their knowledge of networking fundamentals, identify areas where they need additional study, and gain confidence in their ability to pass the exam.
Test-Taking Strategies and Preparation
Maximizing performance on the Network+ Practice Test N10-008 requires effective test-taking strategies and thorough preparation. This includes understanding the test format, allocating time wisely, and employing active recall techniques during studying.
Effective Test-Taking Strategies
Before the test, familiarize yourself with the exam format, question types, and time constraints. During the test, prioritize questions based on your confidence level, starting with the easiest ones. Use process of elimination to rule out incorrect answer choices. Carefully read the questions and instructions to avoid misunderstandings.
Preparation Strategies
Adequate preparation is crucial. Utilize study resources such as textbooks, online courses, and practice tests. Active recall techniques like flashcards, self-quizzing, and teaching the material to others enhance retention. Simulating the actual test environment during practice helps build confidence and reduces anxiety.
Network Fundamentals
Network fundamentals form the foundation of networking knowledge, encompassing core concepts, protocols, and devices that enable seamless communication and data exchange across networks. Understanding these fundamentals is crucial for network professionals.
Network Topologies
Network topologies define the physical and logical arrangements of devices within a network. Common topologies include bus, star, ring, and mesh, each with its advantages and disadvantages in terms of reliability, scalability, and cost.
Network Protocols
Network protocols are sets of rules and procedures that govern communication between devices on a network. They establish standards for data transmission, error handling, and network management. TCP/IP (Transmission Control Protocol/Internet Protocol) is the most widely used protocol suite for internetworking.
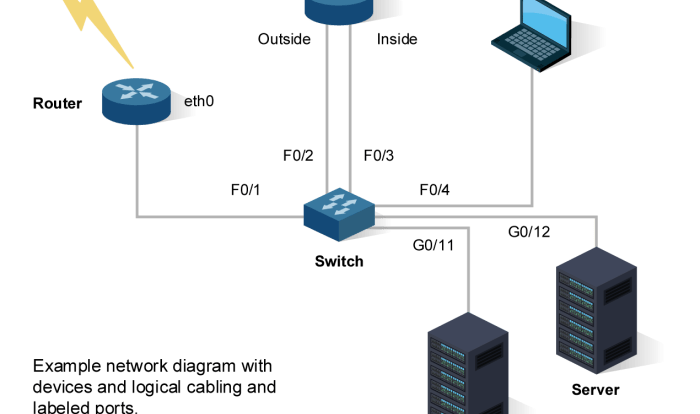
Network Devices
Network devices play specific roles in facilitating communication and data transfer. These include routers, switches, hubs, firewalls, and modems, each serving a unique function in connecting devices, managing traffic, and ensuring network security.
OSI Model
The OSI (Open Systems Interconnection) model is a conceptual framework that divides network communication into seven layers, each with specific functions. These layers include the physical, data link, network, transport, session, presentation, and application layers, providing a structured approach to understanding network operations.
Network Addressing
Network addressing assigns unique identifiers (IP addresses) to devices on a network, enabling them to communicate and exchange data. IP addresses are typically represented in dotted-decimal notation (e.g., 192.168.1.1) and follow specific addressing schemes (e.g., IPv4, IPv6).
Subnetting
Subnetting is the process of dividing a large network into smaller subnetworks, creating logical boundaries within the network. It helps optimize network traffic, improve security, and simplify network management.
Routing Protocols
Routing protocols are responsible for determining the best path for data to take through a network. Common routing protocols include RIP (Routing Information Protocol), OSPF (Open Shortest Path First), and BGP (Border Gateway Protocol), each with its advantages and applications in different network environments.
Network Security
Network security is a critical aspect of network management, ensuring the protection of data, systems, and resources from unauthorized access, use, disclosure, disruption, modification, or destruction.
Network security involves identifying and mitigating security threats and vulnerabilities, implementing security measures, and adhering to security protocols and standards.
Security Threats and Vulnerabilities
- Malware: Malicious software, such as viruses, worms, and Trojans, can infect devices, steal data, and disrupt network operations.
- Phishing: Attempts to trick users into revealing sensitive information, such as passwords or credit card numbers, through fraudulent emails or websites.
- Hacking: Unauthorized access to computer systems or networks to steal data, disrupt operations, or install malware.
- Denial-of-service (DoS) attacks: Overwhelm a system with excessive traffic, making it unavailable to legitimate users.
- Man-in-the-middle attacks: Interception of communications between two parties, allowing the attacker to eavesdrop or manipulate the data.
Security Measures and Best Practices
To protect against these threats, organizations implement security measures such as:
- Firewalls: Network devices that block unauthorized access to internal networks.
- Intrusion detection systems (IDS): Monitor network traffic for suspicious activity and alert administrators.
- Encryption: Converts data into a format that is difficult to decipher without the correct key.
- Strong passwords: Complex passwords that are difficult to guess or crack.
- Multi-factor authentication: Requires multiple forms of identification, such as a password and a code sent to a mobile device.
Security Protocols and Standards
Organizations adhere to security protocols and standards to ensure interoperability and best practices:
- SSL/TLS: Encrypts data transmitted over the internet.
- VPNs: Create secure tunnels for remote access to internal networks.
- Access control lists (ACLs): Specify who is allowed to access specific network resources.
Network Management and Troubleshooting
Network management and troubleshooting are crucial for maintaining network performance and reliability. Network management tools and techniques help monitor, configure, and troubleshoot network issues effectively.
Network Management Tools and Techniques
- Monitoring Tools:Track network performance, identify potential issues, and provide alerts.
- Configuration Management Tools:Automate device configuration and ensure consistency across the network.
- Troubleshooting Tools:Diagnose network problems, identify root causes, and resolve issues efficiently.
Common Network Troubleshooting Methodologies
- OSI Model:A layered approach to network troubleshooting, identifying issues at specific layers.
- Divide-and-Conquer Approach:Isolating the network into smaller segments and testing each segment to identify the source of the problem.
Network Management Best Practices
- Regularly monitor network performance and usage.
- Document network configurations and changes.
- Implement automated monitoring and alerting systems.
- Use standardized troubleshooting procedures.
- Train staff on network management and troubleshooting techniques.
Cloud and Virtualization
Cloud computing and virtualization are transforming the way networks are designed, managed, and utilized. Cloud computing offers a scalable, flexible, and cost-effective way to provision and manage computing resources, while virtualization allows for the consolidation of multiple workloads onto a single physical server.
Cloud Service Models
Cloud computing services are offered in three primary models:
- Infrastructure as a Service (IaaS)provides access to virtualized computing resources, such as servers, storage, and networking.
- Platform as a Service (PaaS)offers a platform for developing, deploying, and managing applications, including the underlying infrastructure and middleware.
- Software as a Service (SaaS)provides access to pre-built applications that are hosted and managed by the cloud provider.
Virtualization Technologies
Virtualization technologies, such as hypervisors and virtual machines (VMs), allow for the creation of multiple isolated virtual environments on a single physical server. This enables:
- Resource optimization:Virtualization allows for more efficient utilization of hardware resources by consolidating multiple workloads onto a single server.
- Isolation:VMs are isolated from each other, providing enhanced security and reliability.
- Portability:VMs can be easily moved between physical servers, enabling seamless migration and failover.
Practice Questions and Answers: Network Plus Practice Test N10-008
Prepare for the Network+ Practice Test N10-008 by testing your knowledge with these practice questions and their detailed explanations. These questions cover the core concepts and skills Artikeld in the test objectives, ensuring a comprehensive review.
Network Fundamentals
- TCP is a reliable, connection-oriented transport layer protocol. It guarantees the delivery of data in the correct order and without errors.
- A network mask defines the subnet portion of an IP address. It is used to determine which devices belong to the same subnet.
- A firewall is a security device that monitors and controls incoming and outgoing network traffic based on predefined rules.
Network Security, Network plus practice test n10-008
- Encryption is the process of converting data into an unreadable format to protect it from unauthorized access.
- A VPN (Virtual Private Network) creates a secure connection over a public network, allowing remote users to access private resources securely.
- Malware is malicious software designed to damage or disrupt computer systems or networks.
Network Management and Troubleshooting
- Network monitoring tools are used to monitor network performance and identify potential issues.
- Ping is a diagnostic tool used to test network connectivity by sending echo requests to a target device.
- Traceroute is a diagnostic tool used to trace the path of packets through a network, identifying potential bottlenecks or points of failure.
Cloud and Virtualization
- Cloud computing provides access to computing resources over the internet, offering scalability and flexibility.
- Virtualization allows multiple operating systems and applications to run on a single physical server, optimizing resource utilization.
- Containers are lightweight, isolated environments that package code and its dependencies, enabling portability and efficiency.
Mock Exam and Score Interpretation
To assess your preparedness for the Network+ Practice Test N10-008, it is essential to take a mock exam that closely simulates the actual test. This mock exam should encompass a comprehensive range of topics covered in the official exam.
Before taking the mock exam, familiarize yourself with the exam format, time constraints, and scoring system. This will help you manage your time effectively and optimize your performance.
Analyzing Performance and Identifying Areas for Improvement
After completing the mock exam, thoroughly analyze your performance to identify areas where you excelled and areas that require further improvement. Focus on questions where you struggled or made incorrect choices.
- Review the correct answers and explanations provided for each question.
- Identify knowledge gaps and weaknesses in specific topics.
- Develop a targeted study plan to address these areas and enhance your understanding.
User Queries
What is the format of the Network+ Practice Test N10-008?
The test consists of 90 multiple-choice and performance-based questions with a time limit of 90 minutes.
What topics are covered in the test?
The test covers a wide range of networking concepts, including network fundamentals, security, management, cloud computing, and virtualization.
How can I prepare for the test?
Utilize our practice questions, study materials, and test-taking strategies to enhance your preparation and maximize your chances of success.